A Digital Design Approach for Defeating Data Leakage Hardware Trojans
Abstract: Since the turn of the century many integrated circuit (IC) design houses have outsourced the production of their chips to other countries. This has created a new opening for cyber-attacks: when a firm sends out a design to be manufactured, the trustworthiness of the manufactured IC can no longer be guaranteed. It is possible to insert hardware Trojans directly into a chip during the design and manufacturing process. These hardware Trojans can destroy a chip, reduce performance or even leak sensitive data. For many in the information assurance arena confidentiality is paramount, so the possibility of a hardware Trojan leaking sensitive data is of greatest concern. In conjunction with its partners from academia, the U.S. Air Force has patented and patent-pending inventions for defending against data-leakage hardware Trojans in 2 forms: 1) combinational and 2) sequential logic. Both forms defeat data leakage through a randomized encoding and split manufacturing scheme. This presentation will focus on the combinational method (the sequential version is similar). Experimental work revealed the power and area overheads associated with these techniques; yet, the user’s risk calculus can be such that these overheads become acceptable – especially when there is only a 3% decrease in performance.
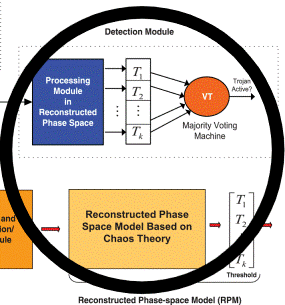
Photo courtesy: H. Zhao et al in IEEE Transactions on Dependable and Secure Computing.
Speaker Bio: Kevin A. Kwiat, PhD, is formerly a Principal Computer Engineer with the U.S. Air Force Research Laboratory (AFRL) with more than 34 years of service. During that time, he conducted research and development in a wide scope of areas: high reliability microcircuit selection for military systems; testability; logic and fault simulation; rad-hard microprocessors; benchmarking of experimental designs; distributed processing systems; assured communications; FPGA-based computing; fault tolerance; survivable systems; game theory; cyber-security; and cloud computing. His PhD is in Computer Engineering from Syracuse University. He is an Adjunct Associate Professor in the Department of Computer Science and Engineering at the University of Buffalo. He is co-founder and leader of Haloed Sun TEK of Sarasota, Florida, which is an LLC specializing in technology transfer and has joined forces with the Commercial Applications for Early Stage Advanced Research (CAESAR) Group. Presently, he is on a hiatus from the CAESAR Group because he was awarded a National Research Council fellowship to investigate hardware security and trust.
Date and Time
Location
Hosts
Registration
-
 Add Event to Calendar
Add Event to Calendar
Loading virtual attendance info...
Speakers
 Dr Kevin A. Kwiat
Dr Kevin A. Kwiat
A Digital Design Approach for Defeating Data Leakage Hardware Trojans
At IEEE: IEEE Xplore
At ACM: Digital Library
At CAESAR Group: AFRL Patent Wall
At Google Scholar: Kevin A. Kwiat
Address:United States

